Updated: 2009-02-12
In this article:
A secure desktop configuration is an important part of any organization's defense-in-depth strategy. But before you can plan for a secure desktop configuration that includes the 2007 Microsoft Office system, you need to understand which security threats are relevant to the 2007 Office system, and then identify which of those security threats pose a risk to your organization's business assets or business processes. You also need to identify which privacy threats pose a risk to users' personal and private information.
Overview of security threats
The security model for the 2007 Office system helps you mitigate six types of security threats. Each of these security threats includes several threat agents and can be exploited by a broad range of security attacks. The following figure shows security threats and examples of the most common threat agents.
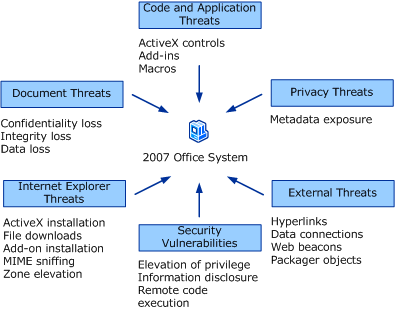
Most organizations face some potential risk from each of the six security threats. However, not every organization faces the same threat agents and not every organization faces the same security attacks or exploits. As a first step in planning a secure desktop configuration that includes the 2007 Office system, use the guidance provided in the following sections to determine:
-
Which of the six security threats are relevant.
-
Which threat agents pose a potential risk.
-
How attackers might exploit these threat agents.
Your organization should have several documents that can help you identify threats in your organization, including threat models, security plans, and operations plans. In addition to the documents that you rely on, be sure to consider the following as you evaluate security threats:
-
Network security architecture (for example, perimeter network design, extranet design, firewall design, and proxy server design).
-
Physical security policies (for example, building access restrictions, document retention policies, and laptop security policies).
-
Privacy policies (for example, definitions of personal and private information).
-
Authentication and authorization infrastructure (for example, how are customers, vendors, or partners granted access to your network).
-
Readiness plan for dealing with sudden security threats.
-
Personal-use policies for e-mail and Internet access.
In addition, be sure to update your organization's existing threat model or security plan if you identify new threats or new threat agents.
Code and application threats
Code and application threats are common desktop security threats. Typical threat agents include ActiveX controls, add-ins, and Visual Basic for Applications (VBA) macros. These threat agents can be exploited by programmers who write malicious code or create malicious programs, which then run on the user's computer. Code and application threats pose a potential risk to organizations of any size. In particular, code and application threats pose a potential risk to your organization if your organization allows users to:
-
Run macros, ActiveX controls, or add-ins.
-
Receive e-mail attachments.
-
Share documents across a public network, such as the Internet.
-
Open documents from sources outside your organization, such as clients, vendors, or partners.
If code and application threats pose a risk to your organization, see Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default security settings for mitigating code and application threats.
Document threats
Document threats occur when unauthorized users attempt to gain access to your organization's documents or the information that is contained in your organization's documents. When unauthorized attackers or intruders gain access to a document, the results can include the loss of:
-
Confidentiality (document data is no longer proprietary).
-
Integrity (document data is altered or corrupted).
-
Content (document data is missing).
Most organizations face document threats, although many organizations choose not to mitigate document threats because the threat is perceived to be minimal or the administrative cost for mitigating the threat is perceived to be high. Nevertheless, document threats pose a risk to your organization when any of the following is true:
-
Your organization's network security architecture cannot keep intruders or attackers from gaining access to your internal network, which increases the risk that intruders or attackers might gain access to your organization's documents.
-
Your organization allows users to send, receive, or share proprietary documents over the Internet, including financial data, project plans, presentations, or drawings.
-
Your organization allows users to connect laptop computers to public networks, which increases the risk that unidentifiable attackers might gain access to the documents that are saved on users' laptop computers.
-
Your organization allows users to take documents that contain proprietary information out of the office.
-
You believe there is a chance that unauthorized attackers or intruders can gain access to documents containing proprietary information.
If document threats pose a risk to your organization, see Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default security settings for mitigating document threats.
External threats
External threats include any threat agent that links a document to another document, a database, or a Web site across an intranet or a public network, such as the Internet. External threats are exploited through the following threat agents:
-
Hyperlinks Attackers typically exploit this threat agent by creating hyperlinks to untrusted documents or Web sites that contain malicious code or content.
-
Data connections Attackers typically exploit this threat agent by creating a data connection to a data source or database, and then using that data connection to maliciously manipulate or extract data.
-
Web beacons Attackers typically exploit this threat agent by embedding an invisible link to a remote image in an e-mail message. When a user opens the e-mail message, the link activates and downloads the remote image. In doing so, user information can be sent to the remote computer, such as the user's e-mail address and the IP address of the user's computer.
-
Packager objects Attackers can exploit this threat agent by having an embedded object execute malicious code.
External threats pose a risk if your organization:
-
Provides users with unrestricted access to public networks, such as the Internet.
-
Allows users to receive e-mail messages containing embedded images and HTML.
-
Allows users to use data connections in spreadsheets or other documents.
If external threats pose a risk to your organization, see Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default security settings for mitigating external threats.
Internet Explorer threats
Internet Explorer threats can occur when an application or a document programmatically uses Internet Explorer functionality. Internet Explorer threats pose a risk to applications and documents because any threats that exist for Internet Explorer also exist for the application or document that is hosting Internet Explorer. Internet Explorer threats include numerous threat agents, and can be exploited through a wide variety of security attacks. Examples of these threat agents include ActiveX control installation, file downloads, Multipurpose Internet Mail Extensions (MIME) sniffing, zone elevation, and add-on installation.
Internet Explorer threats pose a risk if your organization:
-
Allows users to run ActiveX controls, add-ins, or macros that use Internet Explorer functionality.
-
Develops and distributes Office solutions that invoke Internet Explorer functionality.
If your organization faces Internet Explorer threats, see Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default security settings for mitigating Internet Explorer threats.
Privacy threats
Privacy threats include any threat agent that discloses or reveals personal or private information without the user's consent or knowledge. Privacy threats can be exploited through several threat agents, but the most common threat agent is hidden document data, called metadata. Metadata enables users to record or track document properties, such as author name, organization name, document editing time, or document version number. Metadata can be removed from a document, but when it is not, anyone opening the document has access to the metadata.
Privacy threats can also be exploited when a document contains supplemental content that is considered confidential or proprietary, such as comments, revisions, annotations, custom XML data, hidden text, watermarks, and header and footer information. Unless this content is removed from a document, anyone who has access to the document also has access to the supplemental content.
In addition to privacy threats, there are instances in which private information can be disclosed or revealed by enabling or using various application features or functionality. Although these features and functionality are not considered threat agents, they can reveal or disclose personal or private information that your organization deems confidential or proprietary.
For more information about privacy, see the "Privacy Statement for the 2007 Microsoft Office System," which you can access from the Trust Center by clicking Privacy Options, and then clicking Read our privacy statement.
Most organizations face privacy threats or want to actively manage the disclosure of private or personal information. See Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default privacy options or whether you need to change the default security settings for mitigating privacy threats.
Security vulnerabilities
A security vulnerability is a special type of security threat that is addressed by a software update, such as a Microsoft security bulletin or a service pack. Security vulnerabilities can include a wide range of threat agents, such as:
-
Remote code execution
-
Elevation of privilege
-
Information disclosure
Malicious programmers and malicious users can exploit security vulnerabilities through various security attacks. Until a security bulletin or a service pack is released to respond to the security vulnerability, the vulnerability can pose a potential threat to your organization. If security vulnerabilities pose a potential threat to your organization, see "Evaluate default security settings for security vulnerabilities" in Evaluate default security settings and privacy options for the 2007 Office system to determine whether you need to change the default security settings for security vulnerabilities.
Download this book
This topic is included in the following downloadable book for easier reading and printing:
See the full list of available books at Downloadable content for the 2007 Office Resource Kit .

