Updated: 2009-02-12
The 2007 Microsoft Office system has many new security settings that can help you mitigate threats to your organization's business resources and processes. In addition, the 2007 Office system has many new privacy options that help you mitigate threats to users' private and personal information. Determining which new settings and options are appropriate for your organization can be a complex task involving numerous critical planning decisions. To help you minimize the time spent planning settings and options, use the four-step security planning process described in this article. This systematic decision-making approach is designed to help you choose settings and options that maximize protection and productivity in your organization.
The security planning process
Security planning for the 2007 Office system is a straightforward four-step process. Each step provides recommended guidelines and best practices that can help you plan optimal security architecture for your organization's desktop environment. By using this process you can:
-
Determine which tools you need to deploy security settings and privacy options in your organization.
-
Identify the threats that pose a risk to your organization.
-
Evaluate the default settings and options that mitigate those threats.
-
Determine which additional settings and options you need to deploy to minimize risks to your organization's resources and processes.
The security planning process is shown in the following figure.
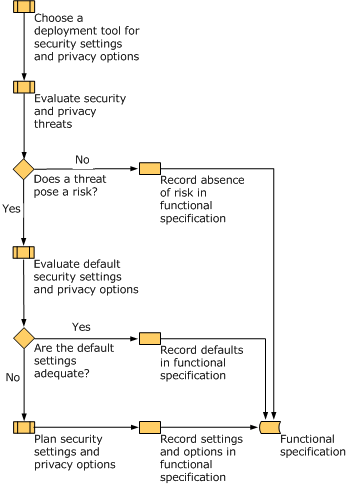
Step 1: Choose a deployment tool for security settings and privacy options
This step helps you choose a deployment tool for rolling out and managing security settings and privacy options. The tools that are discussed include:
-
The Office Customization Tool (OCT), which replaces the Custom Installation Wizard and is the main deployment tool for configuring and managing security settings.
-
The 2007 Office system Administrative Templates (.adm files), which you can load into the Group Policy Object Editor and apply to client computers as local policies or domain-based policies.
Each tool has advantages and disadvantages, and provides different levels of control over your desktop environment. Choosing the right tool to deploy and manage your security settings and privacy options helps ensure that your desktop configuration remains stable.
For detailed information about step 1, see Choose a deployment tool for security settings and privacy options in the 2007 Office system.
Step 2: Evaluate security and privacy threats
This step helps you understand and evaluate security and privacy threats. The 2007 Office system provides settings and options that can help you mitigate six primary types of threats, including:
-
Code and application threats
-
Document threats
-
External threats
-
Internet Explorer threats
-
Privacy threats
-
Security vulnerabilities
Understanding these threats and evaluating threats to determine which might affect your organization are critical in the planning process because so doing enables you to design security settings and privacy options that are relevant to your organization.
For detailed information about step 2, see Evaluate security and privacy threats for the 2007 Office system.
Step 3: Evaluate default security settings and privacy options
This step helps you evaluate the default security settings and privacy options in the 2007 Office system. This step also helps you determine whether the default settings and options provide adequate mitigation for the threats that you identified in step 2. By using the guidance in this step, you can evaluate:
-
Default security threat settings, including settings for code and application threats, document threats, external threats, and Internet Explorer threats.
-
Default privacy options.
-
Default settings for blocking various file formats and file types.
-
Default settings for trusted locations and trusted publishers.
After you complete this step, you should be able to decide whether the default settings and options are appropriate for your organization, or whether you need to deploy additional settings and options that are unique to your organization or your security requirements.
For detailed information about step 3, see Evaluate default security settings and privacy options for the 2007 Office system.
Step 4: Plan security settings and privacy options
This step helps you plan security settings and privacy options. You must plan security settings and privacy options if the default settings and options do not provide adequate protection or do not meet your needs. This step provides recommended guidelines, best practices information, and detailed descriptions of all settings and options. For detailed information about step 4, see the following articles:
Creating a functional specification
The security planning process is designed to help you create a functional specification, which you can use to help you deploy security settings and privacy options. After you complete each step in the planning process, be sure to record your decisions in the functional specification.
Typically, a functional specification for deploying security settings includes:
-
Best practices guidance for using the deployment tools.
-
Overview of the security architecture, including a threat analysis.
-
A list of the settings and options that are being rolled out.
-
Explanations for any settings or options that differ from the default configuration.
At a minimum, the functional specification should provide all of the information an administrator needs to configure security settings and privacy options by using the OCT and by using the 2007 Office system Administrative Template settings in the Group Policy Object Editor.
For more information about functional specifications, including information about using functional specifications with the Microsoft Solutions Framework, see "Planning Phase" in the following white paper: MSF Process Model v. 3.1 (http://go.microsoft.com/fwlink/?LinkId=85569&clcid=0x409).
Download this book
This topic is included in the following downloadable book for easier reading and printing:
See the full list of available books at Downloadable content for the 2007 Office Resource Kit .

